|
Introduction and Customer
Benefits
Seagate Software's visual Internet Support Incident
Tool (VISIT) is a revolutionary form of customer support. Now a
Seagate Software Technical Support representative is only a mouse
click away - waiting to solve your support issues through an interactive
session across the Internet.
By using VISIT, Seagate Software is able to provide
you with superior technical support including:
-
Reduced diagnostic times and resolution times
resulting in fast problem resolution.
-
One-click access to real-time support.
-
A learning experience for you, as a user,
taking part in the interactive session.
-
Multiple technicians participating in a single
session. This makes it easy to escalate and conference with
senior technicians.
-
Easy access via the Internet.
-
Advanced security and privacy features, which
preserve your organization’s firewall security. (The VISIT allows
the delivery of real-time support even when the user and Technical
Support representative are behind different firewalls.)
Top of page
What is VISIT?
Seagate Software's visual Internet Support Incident
Tool (VISIT) makes use of NetManage's SupportNow™ technology, which
is a real-time software support tool.
VISIT brings your support issues directly to
our Technical Support representatives and allows them to provide
faster and more effective technical support. It allows a representative
to see your application on their computer while talking to you on
the telephone.
By being able to see the exact problem, a Technical
Support representative can typically solve your support issues on
the first call. The representative has the capability of escalating
your issue by bringing another senior technician (or team) in to
help solve the problem. The entire session can be recorded for playback
so that you can see the solution and learn how to solve it if it
reoccurs.
Using the VISIT Wizard, the representative can
also view relevant system information such as your operating system,
DLLs in use, and registry keys.
Summary of VISIT features:
-
Interactive real-time visual support sessions.
-
Easy to install and use.
-
Interactive chat allows two-way communication
without the use of telephones.
-
Support for real-time conference escalation.
-
Customer privacy controls.
-
Layered security.
-
Annotated session recording.
-
One-click access to technical support.
Top of page
How does VISIT work?
While communicating with a Technical Support
representative, you can initiate a VISIT session by installing a
small client application and clicking a shortcut to open the connection.
Once the connection has been established, the
Technical Support representative is able to view the desktop on
your computer, and if necessary, be given control of your computer
to fix the problem.
Typical VISIT Scenario
The following diagram presents a typical VISIT
scenario and describes the VISIT process from beginning to end.
Place your cursor over the numbers to learn more about each step
within the process.
-
Telephone Seagate Software to request technical
support.
-
During the call, our Technical Support representative
may suggest initiating a VISIT session. If so, you can install
the VISIT client program on your computer and click the VISIT
shortcut on your desktop to begin the session.
-
Once you begin the session, a VISIT connection
is established and the VISIT Wizard is downloaded to your computer.
The first page of the Wizard opens automatically and asks you
to enter some information. Once you have finished working through
the Wizard, it sends the information that has been gathered
to the VISIT Server.
-
The VISIT Server records your support request
and the information from the Wizard, and displays them on the
VISIT Call Manager Web page.
-
The Technical Support representative connects
to the VISIT Server via the Internet, identifies your request,
and views the support request information. The Technical Support
representative then creates a read-only connection to your computer.
If necessary, you can grant the representative full control
of the your computer.
-
The Technical Support representative resolves
your support issue.
Security Features and Privacy
At Seagate Software it is important to us that
our customers are confident that their computers and associated
data are secure and protected when using our state-of-the-art support
tools.
Seagate Software's visual Internet Support Incident
Tool (VISIT) was developed to meet the needs of the security-conscious
corporation. It empowers you, our customer, to remain in complete
control of the entire support session from beginning to end.
Security features include:
Top of page
Firewall support
The most common and secure way of protecting
private information is with the use of a firewall system.
A firewall system is a collection of systems, routers, and policies
placed at a site’s central connection to a network.
A firewall forces all network connections to
pass through a gateway where they can be examined and evaluated.
The firewall may then restrict access to or from selected systems,
block certain network services, as well as providing other security
features.
VISIT in no way compromises the security of your
organization’s firewall. It has been designed so that you
and the Technical Support representative can interact and work with
each other while remaining behind the security of your respective
firewalls.
Some applications require one or more inbound
ports in the firewall to be opened, which can compromise network
security. Most system administrators will simply refuse to do this.
Rest assured that VISIT does NOT require the customer or the support
organization to open inbound ports in their firewalls, thus preserving
network security.
VISIT makes use of NetManage's SupportNow™ technology,
which has been tested with industry leading firewalls such as Checkpoint™,
Win Route™, and Net Guardian™.
Top of page
VISIT Conference module
Both you and the Technical Support representative
are able to remain behind your respective firewalls because you
communicate and interact through a middle party called a Conference
Module. A Conference Module is a server that is installed outside
our firewall in a Demilitarized Zone (DMZ). A DMZ is a network
area that acts as a security buffer between a private Intranet and
the public.
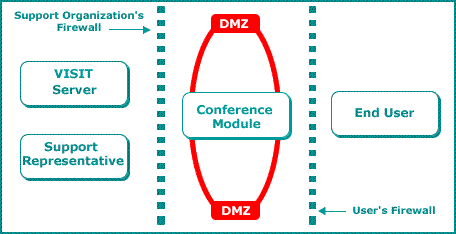
The Conference Module communicates with both
parties via Port 443. Port 443 (which uses the HTTPS protocol or
“HTTP tunneling”) is the secured port that is open by default for
outgoing connections in most corporate firewalls and is the same
secure port through which all e-commerce business transactions are
conducted.
NOTE: If you can make an online
purchase, you can use VISIT.
Top of page
Proxy server support
A proxy server is a server that acts as an intermediary
between your workstation and the Internet so that your corporation
can maintain security and administrative control of Internet access.
VISIT fully supports HTTPS and SOCKS proxy servers.
The VISIT client can easily establish a Support Channel through
a proxy server. During installation, VISIT automatically configures
itself to work with a proxy server if one is being used.
VISIT makes use of NetManage's SupportNow™ technology,
which has been tested with leading proxy servers such as Netscape,
Microsoft, and Apache.
Secure data transfer
VISIT uses a proprietary and comprehensive scrambling
algorithm that encodes all data being transferred. Bitmap
images of the desktop are encrypted and then transferred securely
over the Internet.
Access rights
When using VISIT you maintain complete control
of our Technical Support representative's access rights at all times.
The connection begins initially in read-only mode where our representative
is granted Read-Only access to your computer. In order for the representative
to do anything more than view the screen on your computer, you would
have to grant them Full-Access.
You can switch the access rights of the representative
from Read-Only to Full-Access and vice versa at any time during
the support call by clicking a button.
Top of page
Mouse precedence
At any time during a support session, you can
take back complete control of the session simply by moving your
mouse. This blocks the support representative from making
any further changes. Mouse precedence supercedes any access
privileges that you may have already granted to the representative.
This feature ensures that you have complete control at all times
during a support session.
VISIT Frequently asked questions:
Q: How safe is my data when it is transferred
over the Internet?
A: VISIT sends bitmap images of your desktop
and scrambles them through a proprietary and comprehensive scrambling
algorithm. It would be extremely difficult for someone to
intercept that information and decode it. The use of HTTPS,
the secure protocol used for e-commerce, provides even greater protection.
Q: What will Technical Support representatives
do to my computer?
A: Technical Support representatives can’t
do anything on your computer that you won’t see them do.
You can switch the access rights of the Technical
Support representative from Read-Only to Full-Access and vice versa
at any time during the support call. To regain control of your computer,
simply move your mouse and the application automatically reverts
to Read-Only mode. The support representative can still see what
you are doing and make suggestions.
Q: Will Technical Support representatives
be able to connect to my computer without my permission?
A: No! You are the only one who is capable
of establishing a VISIT session. There is no way to connect to your
computer until you launch the VISIT application and request a connection.
Q: How does this compare to an on-site
service call? Wouldn’t an on-site visit be more secure?
A: We honestly believe that a VISIT connection
through the Internet provides you with more security than an on-site
visit. Not only that, it provides you with service that is faster
and more convenient for you.
With VISIT you can have our Technical Support
representative connect in Read-Only mode, and then continue with
your work while he or she resolves the issue without your constant
supervision.
The following table compares the features offered
through VISIT and On-Site support.
|
Feature
|
VISIT
|
On-Site
|
|
Representative’s access can be limited
to Read-Only mode.
|
Yes
|
No
|
|
Representative's access can be limited
to a single application
|
Yes
|
No
|
|
A record can be kept of all the Representative's
actions for security purposes
|
Yes
|
No
|
Top of page
|


